Lexar JumpDrive 2GB. Part. 2. Lexar Secure II. (Data Security, USB and Flash)
We go on with the review of the Lexar JumpDrive flash drive with embedded disk encryption software Secure II. It is the component of the USB flash drive and is pre-installed in the Ceedo main menu.
So, The Main Menu Lexar Secure II:
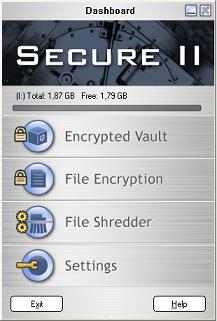
After starting Secure II, we see its main window with three main functions: Encrypted Vault , File Encryption and Shredder.
Encrypted Vault offers a disk encryption based on the file-container and transparent on-the-fly encryption.
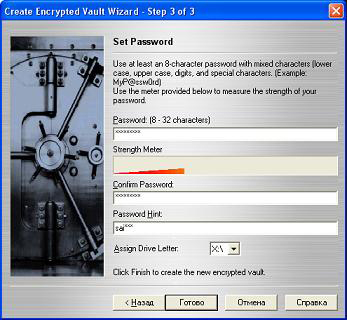
The creation of the virtual disk is fulfilled in 3 steps. At the last stage the Program enforces the user to enter the password of at least 8 symbols (!!). The password should be entered each time when you want to mount encrypted disk.
The program allows to create several disks:
In order to access (open) encrypted disk you should open Ceedo and start Secure II there, or to start it right from USB drive (file SecureII.exe may be copied from the folder F:\SecureII\Windows into the root of the USB flash drive for quick start-up). Further you should indicate what file (disk image file) to mount and to enter the password.
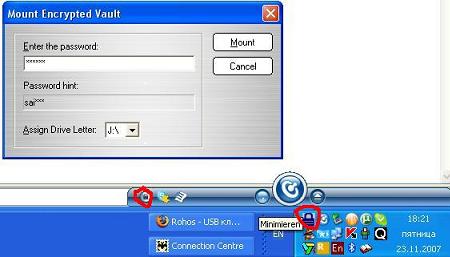
After disk opening the program immediately starts the Explorer for this disk.
Opening of the secret disk was checked at WindowsXp/2000/Vista and everything is functioning. The maximal size of the secret disk and other options were not tested. But in general they do not exist:
• The encrypting algorithm is not indicated (probably AES256)
• The disk letter and its size may not be changed
• The disk is connected as a removable drive (in Rohos Disk as a fixed one)
And to open a secret disk under the Guest account (without administrator privileges) – this is not possible.
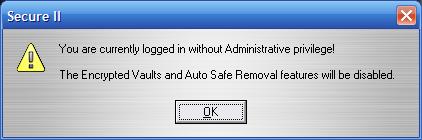
The program does not support this.
Summary: The program is acceptable USB drive protection by the password. But there are some drawbacks:
- Usability: 1) Many clicks are required to access secret disk. 2) The program forces to use the password of at least 8 symbols. The password length is an important parameter for data protection, but manufacturer should not enforce the user, IMHO.
- It is not possible to enlarge encrypted disk, even if you have free space on USB drive. The only solution is to create one more disk.
- If you need to urgently switch off the secret disk, but there are programs working with it, it is not possible to switch off the disk! But if you just pull out the USB drive the secret disk and the program itself will switch off very fast.
- The program does not work without the Administrator privileges. If you decided to go to the Internet-café you should forget about any secret files on it.
Analyzing the arsenal of the given application we could not find anything interesting that would worth our attention. The most important for us were the points 1, 4, 5. We consider them to be the most important also in our program Rohos Disk and we draw much attention to it.
Quickly looking through the functions “File Encryption†we became assured that password protected WinZip is much better anyway. The Shredder also turned out to be not very convenient, so we make a conclusion that these functions are as a loading for the Marketing Attack to the customer.
P.S. The ceedo ‘mobilization’ supports only a limited range of applications of a given versions. Also the drawback of this idea is that Application should exist on a Guest PC.
Our next experiment with Ceedo will be: moving Ceedo into Portable Rohos Mini Drive and launching it from there.
