Rohos Logon Key v3.4 with Active Directory support
Updated: 15 January 2019
Dear users and customers, we are glad to announce first release for a major update of Rohos Logon Key for Windows. Now Rohos Logon Key automatically detects Active Directory environment and uses Active Directory storage to keep domain-wide settings and list of authentication keys and devices. We have completely refactored Rohos Remote Config utility and Key manager. Applying multi-factor authentication in Active Directory has never been so easier!
What’s new in Rohos Management Tools
Added Active Directory Application Partition support. This brings centralized domain-wide settings management and multi-factor authentication media control. Rohos takes advantage of the data storage technology offered by MS Active Directory by creating an AD Application Partition to store all its 2FA configuration data and domain-wide settings. Rohos does not add or change any schema properties on the “user” or other built-in objects in Active Directory. All 2FA data is stored separately in the “DC=Rohos, DC=com” Application Partition.
The list of changes:
- Rohos Remote Config now automatically creates and manage Rohos partition (database) in Active Directory.
- Now you can change any Rohos Logon Key settings across the domain and it will by applied immediately on next authentication attempt on a workstation.
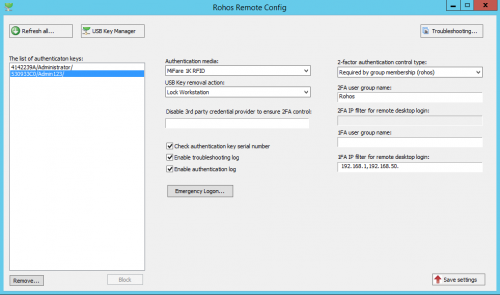
- Rohos Remote Config displays the list of allowed authentication devices by serial number and assigned user name and allows to remove or block the key from the list thus preventing any further authentication by using this device.
- Rohos Remote Config allows to export and import the list of all authentication devices of any type (Google Auth, PKCS#11, Yubikey etc).
- Rohos Remote Config allows automatically creates Rohos database replica on the current Domain Controller.
- Rohos Key Manager allows to setup authentication key and automatically save it’s serial number and user name into the list of allowed Keys located in rohos database in Active Directory.
Domain-wide settings includes: the type of 2-factor authentication policy (all users, by group membership, by IP address) the type of allowed authentication media, Emergency logon Q/A, Rohos Logon settings , etc.
What’s new in Rohos Logon Key:
Rohos Logon automatically detects Active Directory during install and uses it’s settings from the domain:
- Each time during user authentication procedure Rohos reads setting from the Active Directory.
- On each 2 factor authentication attempt Rohos verifies authentication media serial number or device id by using the list of allowed devices from the Active Directory database.
- Added ‘Offline mode’ support that allows to perform 2FA by used cached credentials, local user account or disables Windows login at all.
- Logon icon text and icon is customable from Rohos Remote Config.
These changes do not affects Rohos functionality when installed on a standalone PC with Windows 7/8/10.
Rohos database in Active Directory
Rohos takes advantage of the data storage technology offered by MS Active Directory by using an Application Partition to store all its 2FA configuration data and domain-wide settings. Windows Server hosts this database and also uses this method to store entire AD catalog data.
The first installation of Rohos Managements Tools on a Domain Controller in your enterprise will automatically create this partition. Rohos does not add or change any schema properties on the “user” or other built-in objects in Active Directory. All Rohos data is stored separately in the Rohos Application Partition only. Importing the Rohos schema elements will have no impact on existing objects and replication settings since these objects are not affected.
Rohos partition’s name is: “DC=Rohos,DC=Com”. You can browse and change the partition content with the ADExplorer utility provided by Microsoft.
Please note, uninstalling Rohos does not remove the Rohos data partition. You can delete it only manually by using MS provided ntdsutil.exe utility.
Rohos Remote Config utility
When you first start the Rohos Remote Config, the application will automatically connect to the Active Directory instance on the local machine and prompts to create Rohos 2FA database and store default 2FA settings.
Please note you need to have Domain Administration and Domain Schema Admins and Enterprise Admin permissions in order to run Rohos Remote Config for the first time.
System requirements:
- Windows 2008 R2 / 2012 / 2016 domain controller with schema master role (first install);
- PowerShell v2 or higher installed on Windows Server;
- AD Administration account with Domain Schema Administrator, Enterprise Admin as well as Domain Admin permissions in order to run Rohos Remote Config for the first time.
New settings:
Enable Rohos in credentials prompt dialog
Allows to hide Rohos icon from Windows UAC prompt when running “Run As Admin” commands
Emergency Login
A set of Q/A that allows to bypass 2FA requirements in order to login for any user accounts.
Licensing
Allows to enter license key(s) that will be used across all of the workstations where Rohos Logon Key is installed.
2FA/1FA IP filtering for Remote Desktop logon
Allows to enforce 2FA/1FA by using IP address filtering.
2FA for local accounts
Allows to set 2FA requirements for local accounts on a domain workstations. After you set the name(s) here you can setup a Key for that user name.
Offline Mode
Allows to support 2FA for workstations that goes away\offline from the AD network.
2FA Auditing
“Enable authentication log” and log bad 2FA attempts, log bad PIN attempts
2FA database replication
To support 2FA redundancy it is recommended to setup 2FA database replica on secondary Domain Controllers. When installing Rohos Remote Config on any other DC, it automatically detects existing Rohos database and allows to setup a replica on the new Domain Controller. The replication setup is done via SetReplica.ps1 (located at “C:\Program Files (x86)\Rohos\” )
Or it could be done by a command line:
ntdsutil
partition management
connections
Connect to server SERVERNAME
quit
list nc replicas DC=Rohos,DC=com
add nc replica DC=Rohos,DC=com NULL
Or
ntdsutil “pa m” co “co t s SERVERNAME” q “list nc replicas DC=Rohos,DC=com” “add nc replica DC=Rohos,DC=com NULL”
(where SERVERNAME is the current secondary DC name where you run this command line)
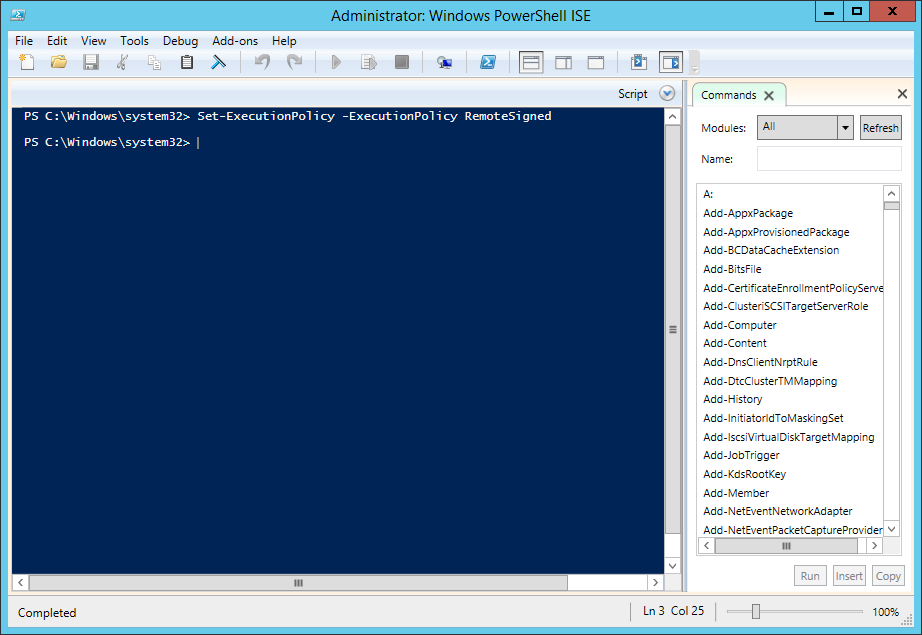
Rohos Remote Config uses powershell script for this operation require. Therefore it should be enabled on DC by opening running “Set-ExecutionPolicy -ExecutionPolicy RemoteSigned” command in “PowerShell ISE (x86)”.
Backup and Restore
Rohos Remote Config allows to backup and restore Rohos database as XML file. Use Tools > Backup command. The backup process uses PowerShell script located at “C:\Program Files (x86)\Rohos\ExportAD.ps1”
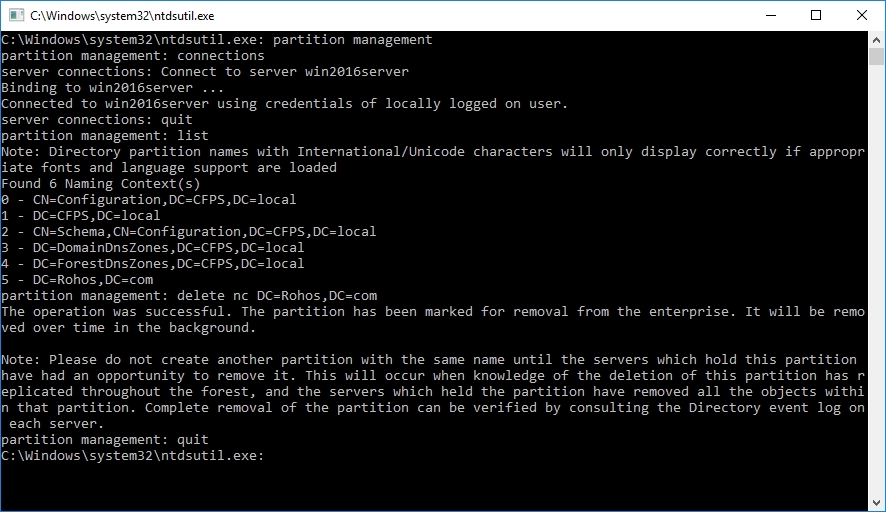
Deleting 2FA database from Active Directory
On the domain controller, where the database was created execute:
ntdsutil
Now you have to consequentially execute the following commands:
partition management
connections
Connect to server %servername%
quit
list
delete nc DC=Rohos,DC=com
quit
quit
Troubleshooting
Just in case of any issues please use Tools > Troubleshooting command to get troubleshooting information.
The list of 2-factor authentication media support
Currently there is a full support for the following devices:
- USB flash drive
- PKCS#11 compliant HSM tokens like iKey, eToken etc.
- MiFare RFID tags
- RFID tags like Indalla, EM Proximity
- Yubikey by public identity, a Key + user Password 2FA configuration is recommended.
- Google Authenticator OTP codes for Remote Desktop or local console login into workstations as well.
We are working to add other security devices and One-Time-Password technology support for Active Directory: U2F security keys, RSA SecureID OTP technology.
How to start with Rohos Management Tools
- Download and Install it on a Windows Server Domain Controller with schema master role.
- Open Rohos Remote Config utility and create Rohos database in Active Directory (or next server it will prompt to create a replica of Rohos database).
Note: Ensure that your Administration account has a Domain Schema Administrator, Enterprise Admin, Domain Admin permissions.
Later: You can install Rohos Management tool on a local workstation with AD administration credentials to continue configuring Rohos and authentication devices after the Domain DataBase is created;
- Set up settings :
- Choose the type of authentication media that will be allowed on workstations.
- Choose 2FA policy : For everyone, by group membership, for Remote Desktop connections or mix.
- Create AD user group and enter it in “2FA user group name” field if you wish to apply 2FA for this group of users
- Enter “2FA filter for Remote Desktop login” if you wish to apply 2FA only by IP filter. Example of filter: “192.168.,192.56.”
- Enter “1FA filter for Remote Desktop login” if you wish to disable 2FA by IP filter.
- Setup Emergency logon if you need to provide a recovery way for Windows Logon in case of authentication media lost.
- Click “Save Settings” to save new settings and apply it for all workstations when Rohos Logon Key is installed.
- Click on “Rohos Key Manager” to start creating authentication keys.
or Start Rohos Logon Key app > Setup Authentication Key – if you are going to use OTP by Google Authenticator. - Done.
2FA by using OTP on Active Directory workstations
We have added experimental support for Google Authenticator for Domain workstations with centralized OTP 2FA setup. Offline mode is not supported as yet. Please contact us if you are interested.
Choose Google Authenticator as authentication means in Rohos Remote Config utility , setup 2FA user in Rohos Logon Key > Setup Authentication Key. Done!
Currently OTP 2FA is supported only on Windows Servers (Remote Desktop login, local console login) with OTP configuration replication across AD network. In order to apply OTP 2FA on new server just install Rohos Management Tools + Rohos Logon Key on it. And the 2FA configuration will be replicated on that server.
Download 15-day trial: