Two-Factor Authentication bypass prevention control in Rohos Logon Key 4.8
We are glad to announce Rohos Logon Key 4.8 with automated prevention over ‘Two-Factor Authentication bypass scenarios’. The new experimental feature allows to get an immediate push notification on the smartphone when the Two-Factor Authentication (2FA / MFA) procedure is avoided during login/unlock or reconnecting to console or remote sessions. Because of well-known system vulnerabilities that allow RDP session hijacking, never-ending stories with 0-day exploits in RDP protocol or authentication system, and unattended remote tools like TeamViewer or 2FA credentials theft during fishing and social engineering – all these lead to unpredictable threat models and risks.
Rohos Logon commits to experimental innovation to address these issues. Currently, Rohos Logon Key app uses three simple rules to trigger push notifications and lock the session in case of Two-Factor Authentication bypass. This allows for defining response and mitigation in case of unknown vulnerabilities of the authentication procedure. The experimental approach works well for standalone Terminal Servers, AD farms, cloud servers in AWS or Azure, workstations, or personal laptops as well. In the future, we plan to add more rules and response actions that allow mitigating authentication vulnerabilities of Windows system, Rohos or human factors. Currently, Rohos Logon Key is the only 2FA application in the world that offers self-control backward loopback, starting from the login prompt to the RDP session desktop. Read more about how it works.
Whats new in Rohos Logon Key 4.8:
- Experimental ‘Two-Factor Authentication Bypass’ control feature
- Rohos Logon Key for Android update with push notifications.
- Minor improvements
Preventing Two-Factor Authentication Bypass – how it works
When the option is enabled, Rohos Logon application uses three rules to detect a bypass or suspicious of 2FA procedure, during any session login, unlock or reconnect, in console or remote desktop:
- For any user login performed without using 2FA credentials by using Rohos Logon Key control (i.e. Rohos login form).
- For a user account with an assigned 2FA method/device – but the session desktop is being created without Rohos 2FA credentials, OR – the remote desktop client IP address differs with the previously detected IP address.
- For any user account where the session is unlocked or reconnected without using Rohos Logon Key control (session hijacking or Rohos 2FA control is being deactivated for some reason).
The rules are constantly being verified by additional independent module by inspecting all desktop sessions (including Remote Desktop sessions). When the rule matches the criteria, Rohos app call push URL API to deliver an immediate push notification on a smartphone, with information about Time, Server name, IP address, and user account name.
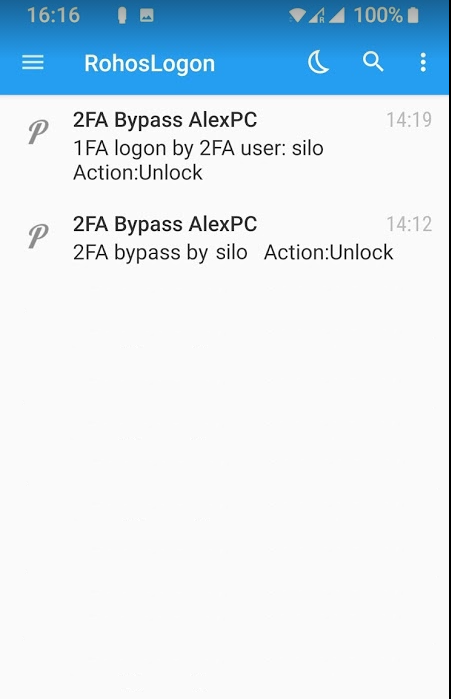
How to setup 2FA bypass notification
Download latest Rohos Logon Key v.4.8 (15-day trial) >>
- Install and Update over existing Rohos Logon (minor update is free). After you setup 2FA method/devices, you need to select the option “Control 2FA bypass… “
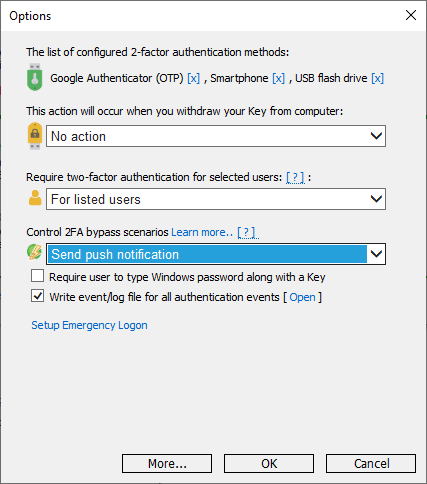
2. Click More.. and enter your Push token URL , currently Rohos Logon support Pushover push service or Rohos Logon Key for Android app.
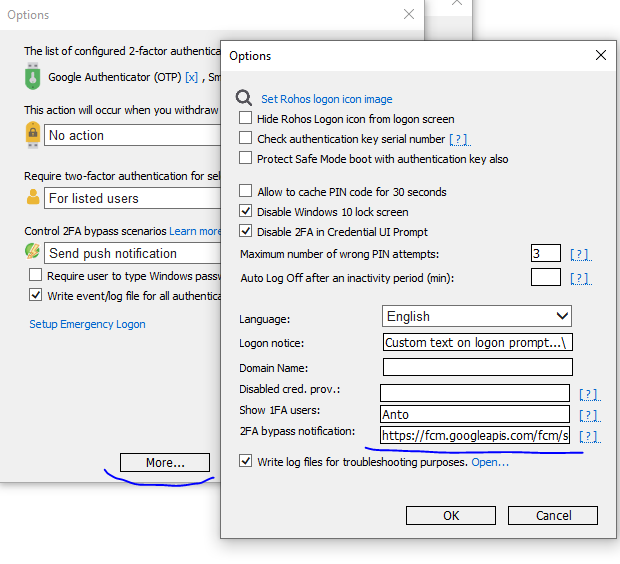
This requires you to register at Pushover service and install Pushover app on your Andorid/iOS smartphone. Then you collect your push service URL from the dashboard and set it into Rohos field.
The URL should looks like the followgin example:
https://api.pushover.net/1/messages.json?token=a1wjrzbuxfgcmhvqbqhfuhxjkft18n&user=*************&device=YourSmartphoneName&title=TS-Server01+Alert&sound=none
where “user” value is taken from the pushover dashboard. “device” is your smartphone name where Pushover app is installed for your account. The service is free for up to 10000 notifications per month. “Token” value represents RohosLogon Key app but you also may create your own app in the dashboard and substitute token value.
In order to test rule #2 you need to login into user account protected with 2FA device, by using Emergency Logon.
In order to test rule #1 you need to change “USB_Key_bypass_control” value to “7” (at HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Rohos) and then login into ANY user account by using Windows password only.
In order to test rule #3 you need to login into user account protected with 2FA device, and then after 5 minutes, connect to the session by using TeamViewer, AnyDesk or alternative remote session application.
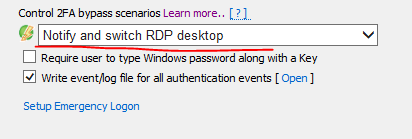
Two-Factor Authentication bypass response action
Instead of notification, it is possible to allow Rohos to immediately lock the user session in case of 2FA bypass scenario. To program this select respective action in Setting, dropdown menu –
About Rohos Logon Key

Rohos Logon Key adds strong two-factor authentication for Windows login and safeguards to prevent 2FA / MFA bypass. Rohos allows implementing multi-factor authentication decision solution, where you can combine different authentication devices: password, PIN code, Smartphone or strong authentication devices like U2F key, YubiKey, Google Authenticator One-Time password codes, SafeNet iKey tokens or RFID cards. With Rohos you can protect standalone computers, Active Directory workstations or Terminal Servers that work over RDP or other remote assistance solutions like TeamViewer or AnyDesk.
Get your copy of Rohos Logon Key>
View the complete list of supported 2FA methods for Windows logon>
