- Before you start
- Creating 2FA database with Rohos Management Tools
- Using Rohos Key Manager to configure authentication keys
- Enterprise-wide Google Auth, OTP configuration
- Installing Rohos Logon Key
- Licensing
Rohos Logon Key application supports standalone workstations as well as domain joined in Active Directory (AD). In this article we’ll describe the second case, where the Rohos Logon Key in installed over a AD domain to perform strong dual factor authentication for local console logon or remote desktop logon on Terminal Services environments with multiple TS hosts.
Before you start
1. Decide on the type of Authentication method you are going to use : hardware security device, OneTimePassword generator or UID RFID card. Ensure that it could be used in Active Directory environment with centralized Key management and also with Remote Desktop connection if applicable.
2. Understand the types of 2-factor authentication (2FA) control policy you can implement with Rohos:
- By AD user group membership : All users included into a specially created Active Directory group will be required to perform two-factor authentication in order to login/unlock workstation; This is the recommended option;
- For the listed users – the list of users who will be required to use dual factor authentication, it is stored in AD 2FA Partition.
- For Remote Desktop users: only remote desktop sessions will be subject to dual factor authentication. The additional IP filtering is also possible to use.
Creating 2FA user group in Active Directory
For example, we can create a domain with DNS-name AMP.local and NetBIOS-name AMP. Let’s assume, a user with name Admin1 must
log in only by 2FA authentication method, the authentication only by the password is forbidden for him. We have to create a new group with a special name, 2FA_users for example and add user Admin1 there. So, this user will be a member of two groups at the same time: Domain users and 2FA_users.
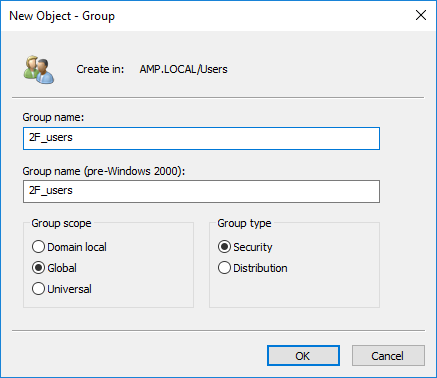
Note: You can choose another name for the group with 2-factor authentication.
Creating 2FA database in Active Directory
Rohos takes advantage of the data storage technology offered by MS Active Directory by creating an AD application partition (database) to store all its 2FA configuration data, user list, devices list and other domain-wide settings of Rohos. Adding additional 2FA schema elements will have no performance impact on other AD/LDAP objects. Learn more…
- Install Rohos Management Tools on your primary AD domain controller with schema master role (FSMO);
- Rohos Remote Config will prompt to create 2FA database in Active Directory, click YES.
- To check if current DC has FSMO, use “netdom query fsmo” command line.
- Later you also need to install Rohos Management Tools on secondary DCs to replicate 2FA settings on it in order to add redundancy for it according to Active Directory principles. Rohos Remote Config will automatically prompt to create 2FA database replicate on the secondary DC.
- Launch Rohos Remote configuration utility and confirm to create an AD database for Rohos Logon Key 2FA options;
- Setup 2FA options:
2FA Authentication device/method,
2FA control type,
2FA group name to hold the list of 2FA users.
Local accounts 2FA control, etc. 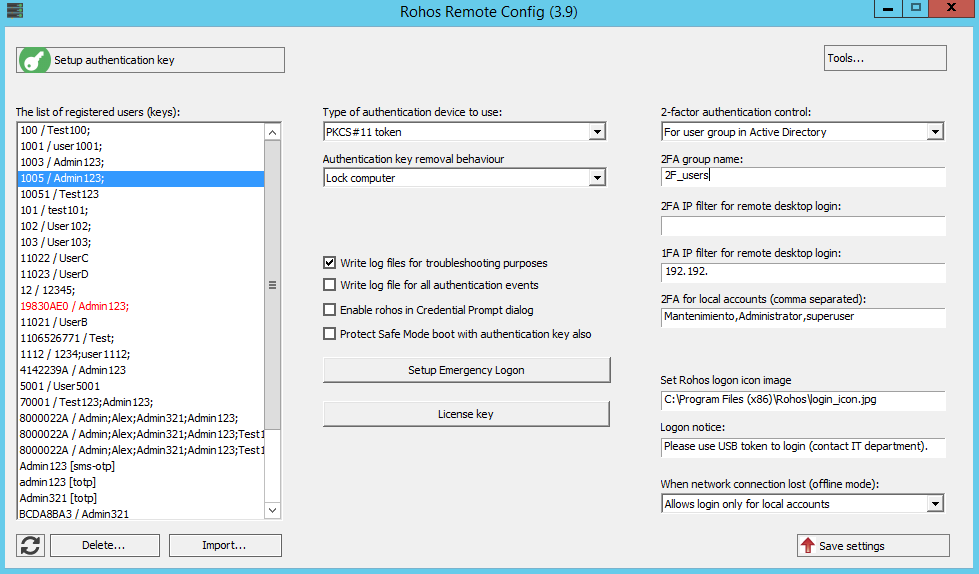
- Rohos Remote Config also display the list of 2FA devices associated with user accounts, so you can choose particular 2FA means,
and save this setting;
Later, You can install Rohos Management Tools on a local workstation
with AD administration credentials to continue configuring Rohos and
locally attached authentication devices; - Click Setup Authentication Key to start configuring authentication keys or methods for any user.
After all the authentication keys were created for a target user group click Refresh all in
Rohos Remote config utility and you will see all the keys, created in
the 2FA database.
Read more about the Rohos Management Tools>>>
Using of Key Manager to configure authentication keys
Click “Setup Authentication Key” to launch Rohos Key Manager utility or OTP configuration dialog (depending on a primary 2FA method).
You need to decide on two-factor authentication vs password replacement solution. With Rohos two-factor authentication types are:
- Authentication device or OTP method + Windows password;
- Authentication device + PIN code;
- Just authentication device – works as a password replacement;
Connect the authentication device. In main window of USB Key manager we can see the list of profiles, stored or associated with the key. Click Add logon profile button.

To edit the profile, select it and press the Edit button. If this key was created before in Rohos Logon Key
application, the password will be encrypted. This profile is not
suitable for the authentication of domain computers. Click in * button
at the right, to show the password. You must change it to non-encrypted
in both fields and click OK.

- If you are not using the AD domain, you can leave the Domain field blank. Then the key will be allowed to log in to all the PC, where this combination of login and password is present.
- If you want two-factor authentication Key + Windows Password then leave password field blank. Then the user will need to use Key + password to login.
You may leave the password field empty, so, a user will be forced to input it
manually during the authentication, along with his Authentication key. The key can
help to identify the user, even if he changes his password.
Centralized enterprise-wide Google Auth OTP configuration.
If you selected Google Authenticator OTP as the primary authentication method.
Click “Setup Authentication Key” will open OTP configuration dialog:
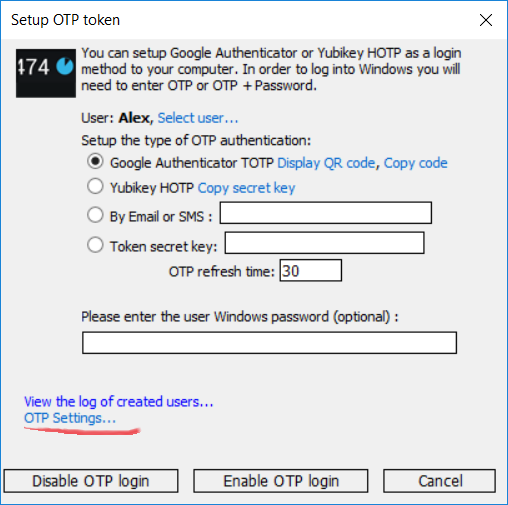
You need to choose user account, OTP method and click Enable OTP login.
Also, it is possible for automated, scriptable configuration of multiple user accounts with Google Authenticator and deliver OTP configuration by email. Read more…
Installing Rohos Logon Key application
Next, in order to apply 2FA control it is required to install Rohos Logon Key
application on each workstation and Terminal Server where you need two-factor authentication. After the installation, Rohos Logon Key application will automatically find the Active Directory 2FA settings, if this computer
is connected to a domain.
Please note that you also need to install Rohos Management Tools on secondary DC to replicate 2FA database on it in order to add redundancy functionality for it according to Windows AD principles. Rohos Remote Config will automatically prompt to create 2FA database replicate on the secondary DC.
Rohos Licenses for domain computers
- Pro license – for each domain workstation.
- Server license – for terminal servers, RDC on Windows 2003, 2008, 2012.
